Note: Kaspersky has informed us that TDSSKiller is not GDPR compliant. You should take this into account if you are located in the EU/EEA and wish to download this application.
In order to ensure smooth running of any computer, the first and foremost requirement is for it to be malware-free, and this can be achieved using an efficient antivirus solution.
Occasionally, though, a dedicated utility is needed to eradicate a specific type of threat, such as TDSSKiller which removes malware from the Rootkit.Win32.TDSS family.
Damages done to your system by rootkits
Rootkits are a special type of malware which run surreptitiously on a computer and modify the behavior of the host PC or of other installed programs. This way, they can take over certain functions and seem legitimate, and collect sensitive information.
Since these rootkits get new variants quite frequently, having a specialized tool like TDSSKiller can help users detect and remove the threat before it does any damage.
Simple scan and deletion operations
The benefit in using TDSSKiller is that users need to simply run the program and press a single button in order for the scanning process to launch. Otherwise, one would need to search the registry for entries affected by the rootkit and erase them manually.
Scan the driver digital signatures
Additionally, TDSSKiller allows users to broaden or restrict the scan, depending on their choices. For instance, if users suspect that the rootkit is hidden within the drivers on their computer, they can set TDSSKiller to scan the driver digital signatures as well.
Reports
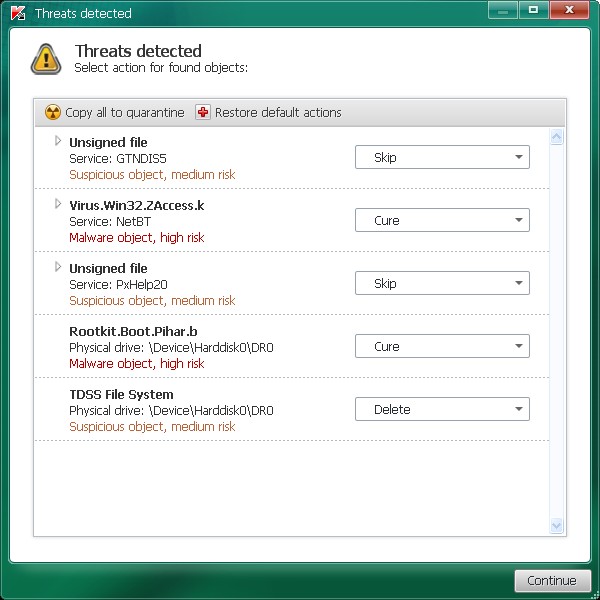
Once the scan is over, the software app will display a brief summary of the results, and experts get the chance to analyze a detailed version of the report if they want additional information about the scan. They can also choose the action that needs to be taken once a threat is detected, if they consider it is a false positive.
Conclusion
The bottom line is that not only viruses are dangerous when it comes to computer security, rootkits can prove to be just as harmful. Nonetheless, keeping the antivirus solution correctly configured and relying on dedicated removal tools when needed will help users keep their PC free of any infection.
TDSSKiller With License Key Free Download [March-2022]
TDSSKiller is a freeware computer security tool that allows users to scan and remove rootkits of the Rootkit.Win32.TDSS family. It uses a two-step approach to rootkit detection, scanning registry and driver entries and using an automatic driver signature scanning technology. Once the scan is over, it displays a brief summary of the results in a tree view. Those who want more information about the scan, can request a full report.
TDSSKiller features:
Scan the registry for any hidden file
Scan driver digital signatures
Extend the scan by changing the rootkit detection settings
Display a brief summary of the scan results
Use an automatic driver signature scanning technology
Use of TDSSKiller requires that the user has administrative rights on his computer.
TDSSKiller Requirements:
Windows XP/7/8/Vista
1 GHz or faster processor
About SecureMyPC
SecureMyPC is a comprehensive security suite for your computer, with many valuable tools to keep you safe. See more at:
Difference between preparing the database in the server or in the client?
In my SQL Server instance we have a few databases and several applications using those databases. We have different deployment policies for the data and the application.
For the application we deploy the different options (e.g. apps, backoffice, customers) in a different way in the different locations and in case of any changes to the application we do a synchronization by copying the binaries and config files between the two locations. So, we have a central deployment database located on the server and each location contains the application databases.
When it comes to the databases, we have a similar deployment model. Different databases are deployed in different environments (e.g. staging, standard, production). In case of a schema change we also have to manually copy the binaries and config files.
To cut the long story short, I am looking into the possibility of using SQL Sync. It looks like a nice solution for the application deployments, but will it solve my problem with the databases?
In case of the databases, I am not looking into the different mechanisms where I store the binaries and config files and how to deploy these files to the different locations of my server (i.e. server1, server2, server3, etc).
I am not looking into the question if I should copy the binaries and config files or create databases with
TDSSKiller Crack+ Free Download
TDSSKiller is a reliable toolkit for detecting and removing ‘TDSS Rootkit’- the most dangerous rootkit malware today. It can find and remove a wide range of rootkit variants from the Registry, including infamous ‘TDSS’ and its latest variants. The toolkit provides users with one-click scan engine and supports automatic detection of all TDSS variants, including all its recent variants, plus detection of all its obfuscation techniques.
Try Premium for 30 Days
Live chat
Customer service is ready to help you
Welcome to the help area of Agoda.com.Our team of experts is at your service to offer assistance in several different ways.
For the fastest response, please choose from the following categories:
Customer service
Feedback for customers
Errors and bugs
Contact us
Agoda is committed to responding to your needs quickly. We are available 24 hours a day, 7 days a week.
You may contact us in the following ways:
Agoda employees are available on the phone (24/7).
Send us a quick email.
Write a short message below.
Live chat
Error messages (bug or technical issues)
Send us your message below.
We’ll get back to you as soon as possible.
Feedback for customers
Contact us
To contact our Customer Service Team, please submit your message below.[Histochemistry of pollen allergens: results of a study of the anaphylactic factor].
The structure of the anaphylactic agent and the mechanisms of the allergies to pollens remain poorly known. Pollen allergen extracts (cat, horse, grass) were treated with proteolytic enzymes; IEF analysis followed by transfer on nitrocellulose sheets were performed. The results are discussed in relation to IgE detection in wheal skin tests (radioallergosorbent test, RAST). Both the allergens and allergenic sites were destroyed by the action of proteases.THE artist concerned with the architecture and design of the future thinks he can have a hand in shaping it. Sheppard Frere is a London-based young man, who has had his work shown in great modern buildings and galleries across the world, and has also been selected as one of our Emerging Young Architects, with whom we are partnering with this spring. In the course of his career, Frere has been
b7e8fdf5c8
TDSSKiller Crack
TDSSKiller is the most powerful antimalware tool available. Its cutting-edge technology and professional support system make it an invaluable asset to even the most experienced IT specialists. The effectiveness of the program is obvious. Besides detecting rootkits, TDSSKiller examines digital files and CDs for the presence of malicious software. The software is easy to use and can quickly find and delete almost any type of infection.
TDSSKiller Features:
Detects and removes rootkits and other types of hidden malware
Monitors and repairs the integrity of the operating system
Blocks malicious or dangerous files and programs
Detects and removs devices infected with rootkits
Finds, displays and removes viruses, Trojans, keyloggers and backdoors
Detects and removes adware
Various custom options
Extend and shrink active scan lists
System Requirements:
TDSSKiller will run on all 32-bit versions of Windows, including the latest Windows 10
How to get TDSSKiller:
Visit the official website of TDSSKiller. Make sure you scan only for rootkits. You can only harm the system.
The rootkit will be found as a driver. That means you will have to open your system admin tools, open the driver folder and find the file that you think is rootkit.
Restore
Select the scan, scan for all (if not selected, select a specific drive), set options (if not selected, select default, tick files, tick extra folders and tick volume protected), now is the time to click the start button.
TDSSKiller will start with your boot drive and will also scan for rootkits in other drives. Have you started to scan?
Scan Complete
You have now scanned the boot drive. The app will display the actual results. Have you found a rootkit or a virus?
Warning
As soon as you see a result, this is your chance to remove it. Choose the drive that you think is infected.
Warning
Tick the file, tick the entries in the folders, and click on yes or confirm.
Warning
No way. The scan can be completed only as a default.
Warning
Now, you have to run TDSSKiller as administrator. Right-click on the TDSSKiller icon and select Run as Administrator. Now click on the Start button.
Warning
Deselect the drive to be scanned.
Warning
Click on the Start button and
What’s New In TDSSKiller?
Get rid of all kinds of hidden threats, including the TDSS family of rootkits. It is a very efficient and easy-to-use malware removal utility designed for Windows systems to help recover from infections like the Rootkit.Win32.TDSS family.
TDSSKiller Usage:
– Press “Scan” to start scanning and remove all detected threats.
– Press “Confirm” to delete detected threats.
– Press “Yes” to get a full report about all detected threats.
– Press “No” to skip this step.
– Press “Exit” to quit TDSSKiller and close the application.
TDSSKiller Functionality:
Get rid of all kinds of hidden threats, including the TDSS family of rootkits.
Scan for hidden threats, including the Rootkit.Win32.TDSS family.
Get a full report of all detected threats.
Delete detected threats.
You can adjust the scan to include only one type of threats, such as rootkits, or a specific file type.
When disabling a scan, the program will automatically set the next time you run it.
The scan takes only a few seconds because TDSSKiller has the ability to detect the malware in real time, and remove it before it does any harm.
01/09/2014
Mean Tweets: See some of them from the Browns’ 2015 Draft class
With the first round of the NFL Draft coming to an end yesterday the Browns, and the rest of the league, are scrambling to see who will be the next great player to fill in the shoes of the Browns incredible drafting success of 2014.
With the first round of the NFL Draft coming to an end yesterday the Browns, and the rest of the league, are scrambling to see who will be the next great player to fill in the shoes of the Browns incredible drafting success of 2014.
With the first round of the NFL Draft coming to an end yesterday the Browns, and the rest of the league, are scrambling to see who will be the next great player to fill in the shoes of the Browns incredible drafting success of 2014.
With the first round of the NFL Draft coming to an end yesterday the Browns, and the rest of the league, are scrambling to see who will be the next great player to fill in the shoes of the Browns incredible drafting success of 2014.
With the first round of the NFL Draft coming to an
System Requirements:
Microsoft Windows XP/Vista/7/8.1
3.5 GB Free Disk Space
1024 x 768 Minimum Screen Resolution (or higher)
DirectX 9.0c compatible with Shader Model 2.0
1024MB RAM (1GB recommended)
Hard disk space 2 GB is recommended.
Keyboard Mouse
From the Main Menu go to the ‘Options’ and select the ‘Video’ tab. “Things could turn.” “Yes, they could.” “I’m sorry, I just can’t marry you
https://sitandbreaktheice.org/pim-xtreme-0-4-1-crack-free-latest-2022/
https://2z31.com/video-cutter-crack-free-x64-updated/
https://verrtise.com/advert/access-passview-crack-product-key-full-mac-win-2022/
https://www.theblender.it/xilisoft-ipad-magic-3-5-1-full-product-key-free-for-windows/
http://shop.chatredanesh.ir/?p=51249
https://zip-favor.ru/laptops/vovsoft-m3u8-downloader-crack-for-windows/
https://endlessorchard.com/msd-tasks-6-00-crack-for-windows/
https://descargatelo.net/wp-content/uploads/2022/07/TV_Show_Subtitle_Automatic_Downloader.pdf
https://genomics.ucsf.edu/system/files/webform/ccglorders/iOrgSoft-DVD-to-Flash-Converter.pdf
https://wakelet.com/wake/_GWfidj_yYtauRRytHZth
https://nashvilleopportunity.com/manageengine-adselfservice-plus-with-product-key-pcwindows-latest/
http://kitchenwaresreview.com/?p=41781
https://x-streem.com/upload/files/2022/07/iliAvwxwJVN5na3JU3Mg_04_b5bfbc36aa31fddb436b4ed2dd39bb4a_file.pdf
https://dogrywka.pl/edwinxp-2-10-crack/
https://ameeni.com/upload/files/2022/07/Aw8gBKzrgRfbXUZhlF71_04_4a0749c25245ee72abb7931c90798201_file.pdf
https://www.pooldone.com/qvision-crack-free-download-mac-win/
https://www.cameraitacina.com/en/system/files/webform/feedback/vasibro500.pdf
https://teenmemorywall.com/autocad-architecture-2-6-2-crack-free-license-key-pc-windows/
http://nuvocasa.com/?p=29152
 Wellness Food Net Good Food and Health
Wellness Food Net Good Food and Health
